Cyber Security and the Opportunist Criminal: Crime by its nature is often an opportunistic endeavour. Even the most detailed, considered and planned criminal enterprise is borne of a person seeing an opening and taking advantage of the opportunity that the opening gives them. The great train robbery of 1963 saw Bruce Reynolds, Ronnie Biggs and co, discover from a Royal Mail employee that huge sums of money were being transferred by train between Glasgow and London. This event created the opportunity that resulted in one of the most famous heists of all time.
While the days of train robberies are perhaps behind us the opportunities presented to criminals are, if anything far more abundant. To the criminal world technology has presented opportunities to get rich quick with far less risk to themselves or the organisations that they work for. I say organisations as the opportunity for Cyber-crime isn’t just perpetuated by teenage hackers sat in dark rooms but also by structured teams and businesses that do this for a living.
It’s not just get rich quick schemes either. The opportunities our technological advances provide are ever increasing. Looking to take advantage of these advances are cyber terrorists, activists (hacktivists), governments and cyber explorers all of whom have their own agendas that can cause untold damage to their targets as well as collateral damage to unintended victims.
A perfect example of this is the ransomware infection that hit the NHS and many other organisations in 2017. The infection was known as WannaCry and was ultimately attributed to an attack perpetrated by North Korea. Dig further though and you’ll find that the origins of the attack ultimately stemmed from the United States’ National Security Agency (NSA). The NSA identified a hole in the Windows operating system (a vulnerability) and held on to that knowledge for over 5 years. In those 5 years the NSA saw an opportunity to use that vulnerability for the benefit of the United States although what they did with it during that time has never been revealed. The subsequent online leak of the vulnerability gave the rest of the world, and specifically North Korea, the opportunity to exploit the problem leading to outages to businesses and individuals across the globe.
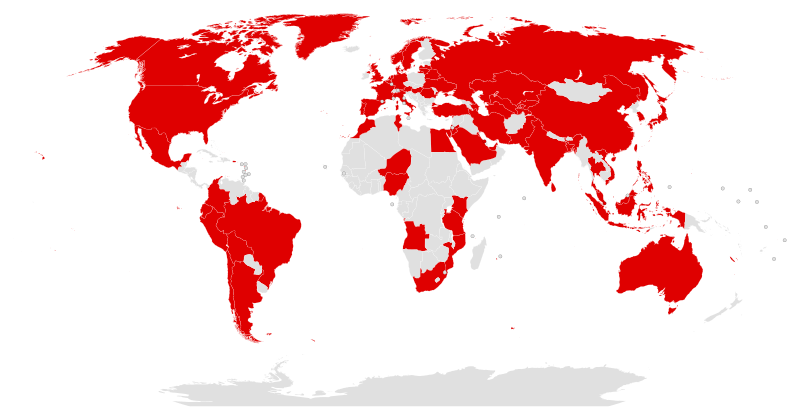
The graphic below shows the countries hit in the initial hours of the WannaCry attack. It’s believed that over 200,000 systems were affected by the attack across 150 countries. All from North Korea taking advantage of an opportunity presented to it by America’s National Security Agency.
And so on to the crux of the post… The current Covid-19 pandemic is a goldmine of an opportunity for all of the cyber criminals out there. It’s a worldwide first on a level we’ve never seen. This creates uncertainty, fear, panic and reactionary situations that will not always result in people and businesses making the right decisions. The uncertainty coupled with vastly different lifestyle and working practices has exposed new potential vulnerabilities in IT security systems for the bad guys to try and exploit.
If you’re one of the businesses that’s looking back on their working from home approach following the lockdown and wondering if you did the right thing, you’re on the right track. Security should always be at the forefront of a business’s technology and working considerations. It’s a constantly moving target and business leaders need to be aware that the opportunists are waiting to take advantage of a bad decision.
Few businesses can afford to lose money at the current time and in the words of Benjamin Franklin “Time is Money”. A malware infection, a data breach or a ransomware outbreak will stop a business from working. In some cases, it’ll slow a business down and others it will cripple them for days or weeks. For the NHS’s it was a week and cost £20 million during the outage and a subsequent £72 million in the clean-up. In the current climate how long can your business stop for while your IT team fixes things, recovers data or liaises with the ICO when the problem could have been prevented in the first place?
There’s no hard sell in this blog post. Just a reminder that this is a time where the bad guys are thriving while business leaders are fighting to keep their businesses alive and their employees working.
If you don’t have an IT team, if your team need external support or if you’re just not happy with the help your existing IT company have given during this time Novem are here. We can answer questions and give pointers and recommendations on how you can improve your business security to reduce and eliminate risk.
You need a business to come back to at the end of the lockdown. Don’t let the opportunist criminal stop you.
Get in touch with us for more information on how we can help you with your cyber security.
